Integrating with Okta
Website Documentation for your KeePass client and Pleasant Password Server
(Versions 7+)
Pleasant Password Server can integrate with Okta which can provide SAML Single Sign On and usage of multiple factors of authentication (MFA).
Integration Methods:
- SAML SSO
- Multi-Factor Authentication (see below)
Okta Supported MFA Types:
- Security questions
- Okta Verify OTP (a token from smartphones)
- Okta Verify Push (an Okta SMS from smartphones)
- SMS (a text to a phone)
- Email as a factor
- Voice
- U2F
- Third-Party: Authenticator Apps, Symantec VIP, Duo Security, RSA SecurID, YubiKey
- Windows Hello
- Apple TouchID
Warning: Be careful when setting Two Factor Required, as it could prevent users from logging in unless:
- Their accounts can be self-enrolled, or,
- they have been individually configured to use at least one 2FA provider (eg. Authenticator Apps).
- If users have already been locked out, please Contact us!
RADIUS
Okta doesn’t support RADIUS natively.
- However, an Okta RADIUS agent can be installed on a 2008 server (potentially new server versions as well)
- A VPN configuration can forward the RADIUS server requests as SSL requests to Okta cloud based authentication servers.
Example Setup
Below is an example of how Okta interacts with a Cisco ASA VPN for Anyconnect RADIUS authentication protocol.
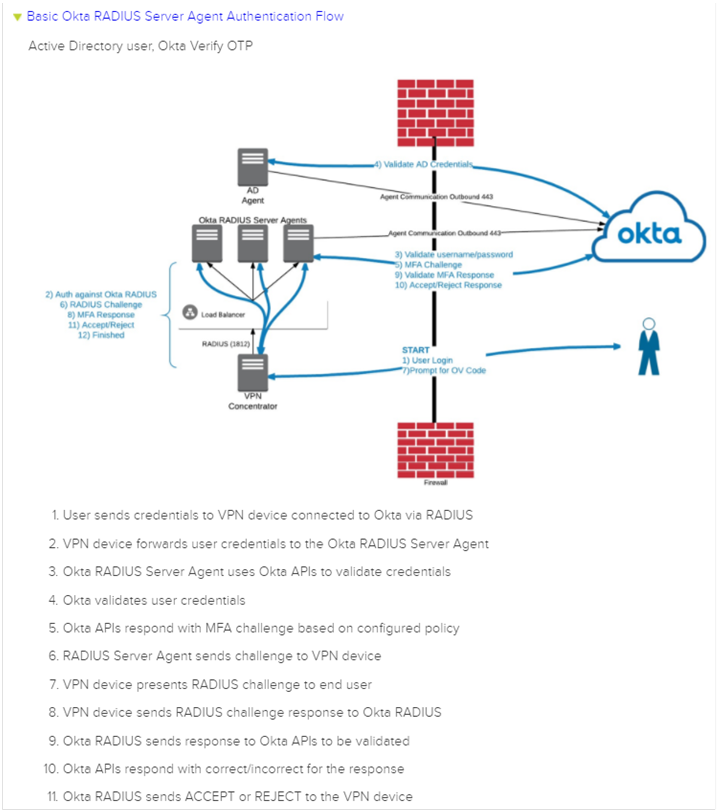
The configuration for Okta is broken into sections: Group Setup and User Setup.
Group Setup
- Sign into Okta as an Admin
- Click Admin button in upper right
-
Click Security -> Multi-factor from the top menu.
-
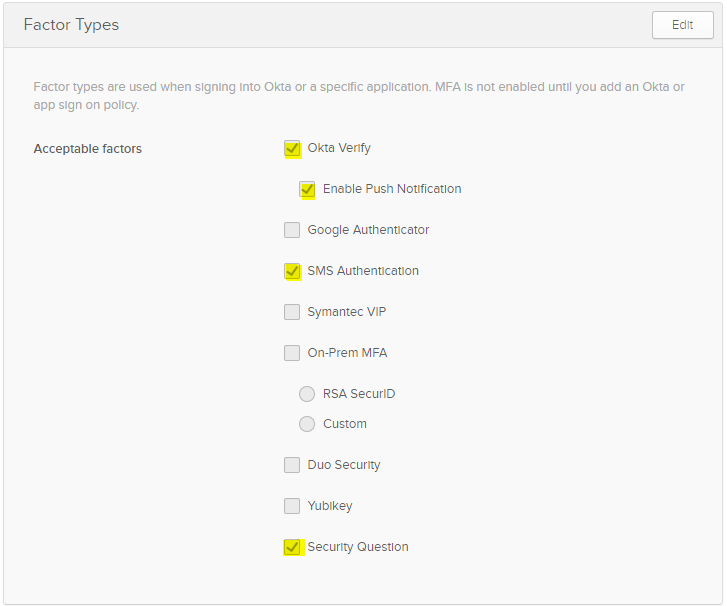
Pick the types of MFA you want Okta to support.
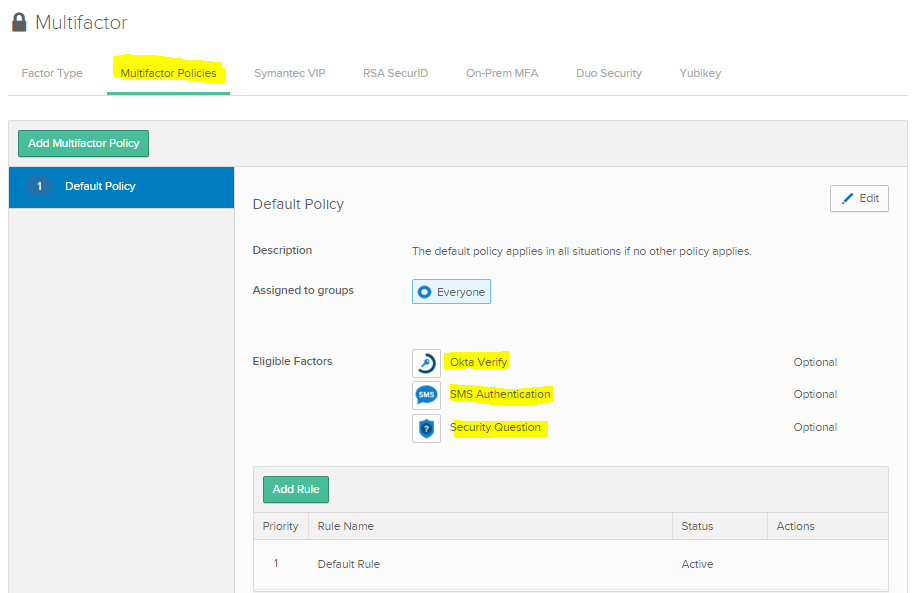
- Next Choose Multi-factor Policies. Adding Okta Verify to this list makes it an available option later in the configuration.
-
Next click Security ->Policies.
- These policies are processed sequentially and stopped at the 1st match. That is why the RADIUS rules were moved to the top since that protocol is new and would not impact any logic in the legacy or default policies below.
-
2 new policies were added. The 1st Policy defines which groups a user needs to be a member of IN ADDITION TO having a valid Okta verify token.
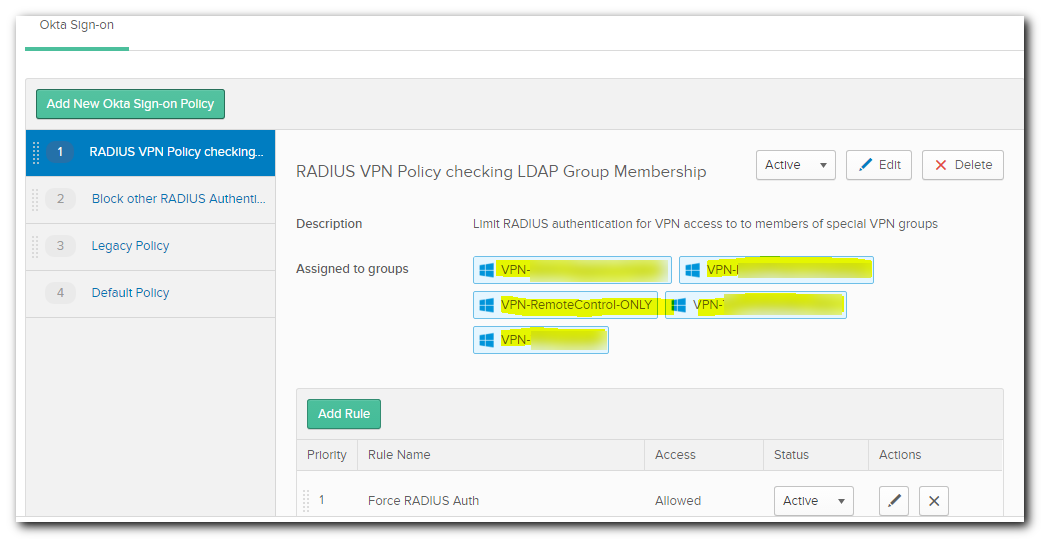
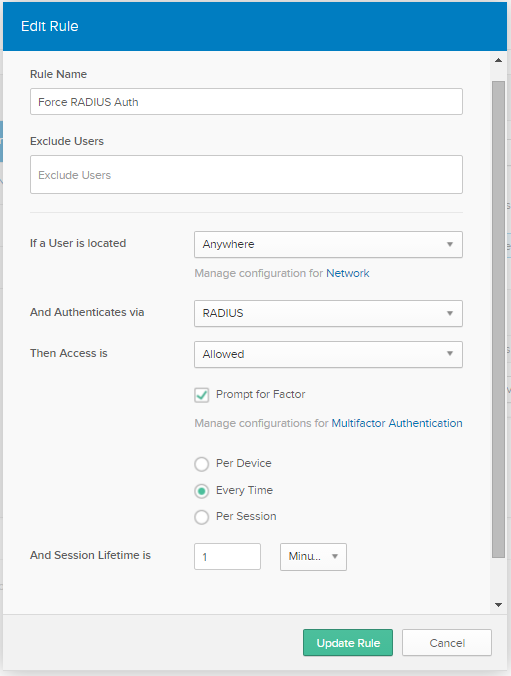
- The rule logic is shown below. It says if you are using RADIUS Authentication AND are a member of a group listed in the “Assigned Groups” you must pass 1 of the 4 forms of MFA every connection attempt, regardless of location.
-
NOTE: Failure to add a newly created group to the above policy may prevent successful logon.
-
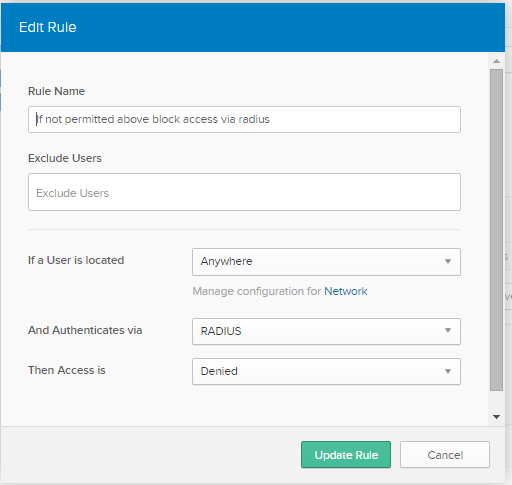
The 2nd policy blocks ALL other RADIUS not explicitly permitted above.
-
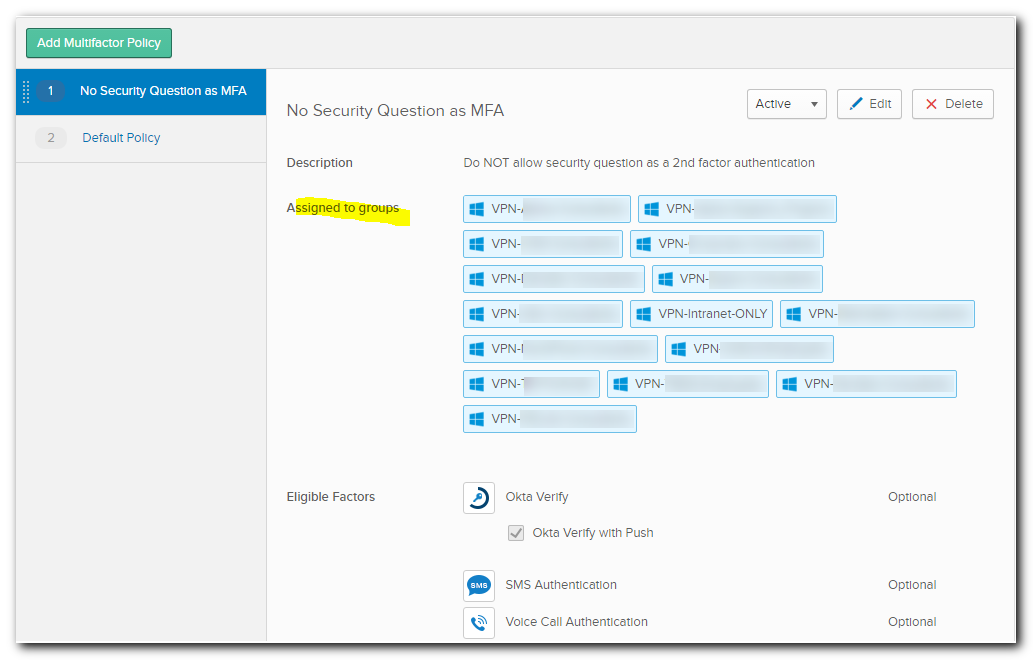
Next click Security -> Multi-factor -> Multi-factor Policies.
-
Edit add new VPN-* group then click UPDATE POLICY. This policy disables security questions as a viable option for these groups.
-
-
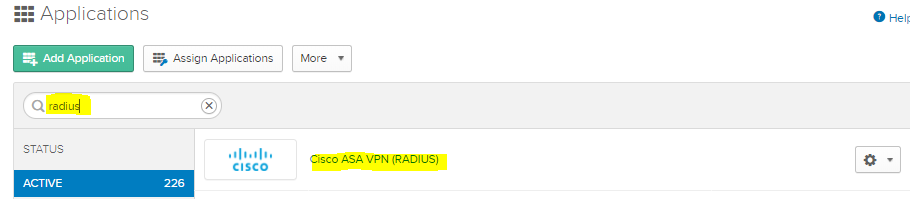
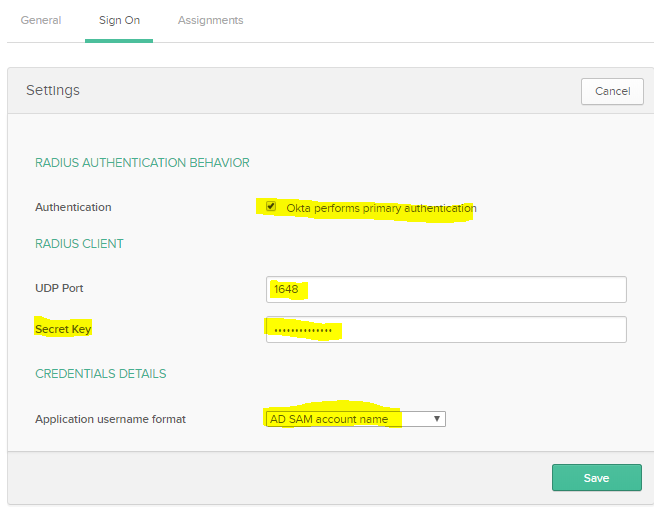
Add Custom RADIUS Application next

-
Accept the rest of the defaults
-
This will not work right away, however. The reason is even though you’ve selected SamAccountName Okta uses DN (ie user.name@internaldomain.com) To fix you need to modify the profile editor and mapping
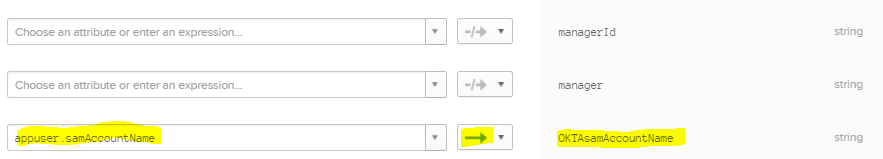
-
You MUST select the green arrow (it will impact new AND existing user profiles) Also click Save Mappings then APPLY button
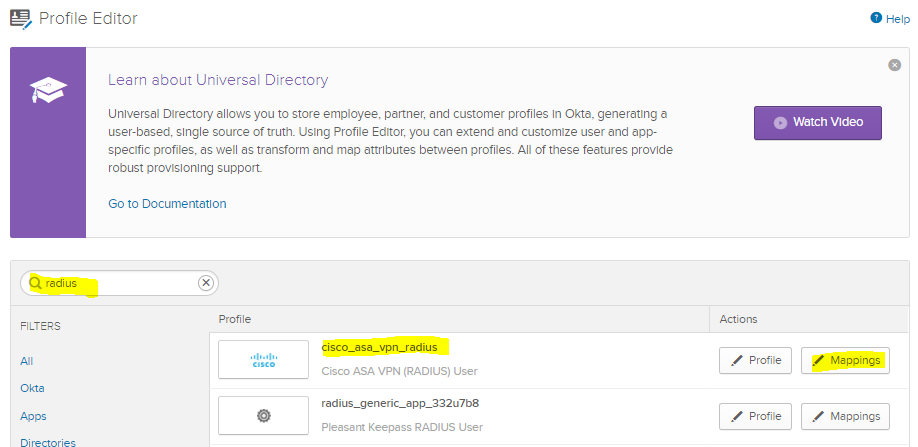
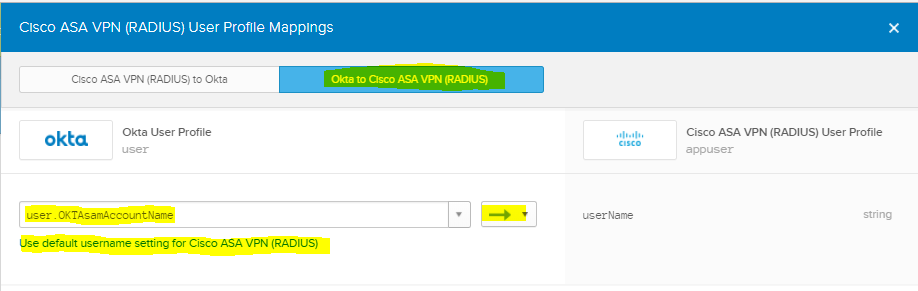
-
That should be all that is required to support Anyconnect RADIUS to Okta & now you can add additional custom RADIUS applications too!
