Setting Up RADIUS
Users prefer Pleasant Password Server with a KeePass client!
(Versions 7.4+)
Password Server supports authenticating against an external RADIUS server as a Two-Factor Provider.
RADIUS Configuration
Most RADIUS setups should have little need for additional configuration. For Password Server to authenticate, you will need:
- A Client - or the Server itself, if desired - that allows authentication requests from the machine that Password Server is running on.
- The shared secret for that Client.
- The Server configured to accept at least one authentication protocol from that Client:
- PAP, CHAP, or MS-CHAPv2
- Note: the EAP protocol may not work
- Users able to authenticate through a single-step logon procedure able to output text into a web form. For example, a static password or most One-Time Password (OTP) Providers will be sufficient.
-
Users with the same username in Password Server as they have in RADIUS. This will likely be the case if both Password Server and RADIUS are importing from the same LDAP server.
Clarification Notes:
- Complicated Authentication procedures involving Challenge-responses, are not yet supported.
- If you use something like a biometric scanner, make sure it can output the necessary data as text.
- The server address is the address of the RADIUS server.
- The NAS Identifier filed is an optional attribute. Some servers require it but if yours doesn't you can ignore it.
Password Server Configuration
In Password Server itself, the configuration is simple.
- Go to Users and Roles > Manage Policies and click the name of the user policy containing the users you want to authenticate against RADIUS.
- Scroll down to Two Factor Policy and look for RADIUS in the configuration list. Click the [Configure] link in that row.
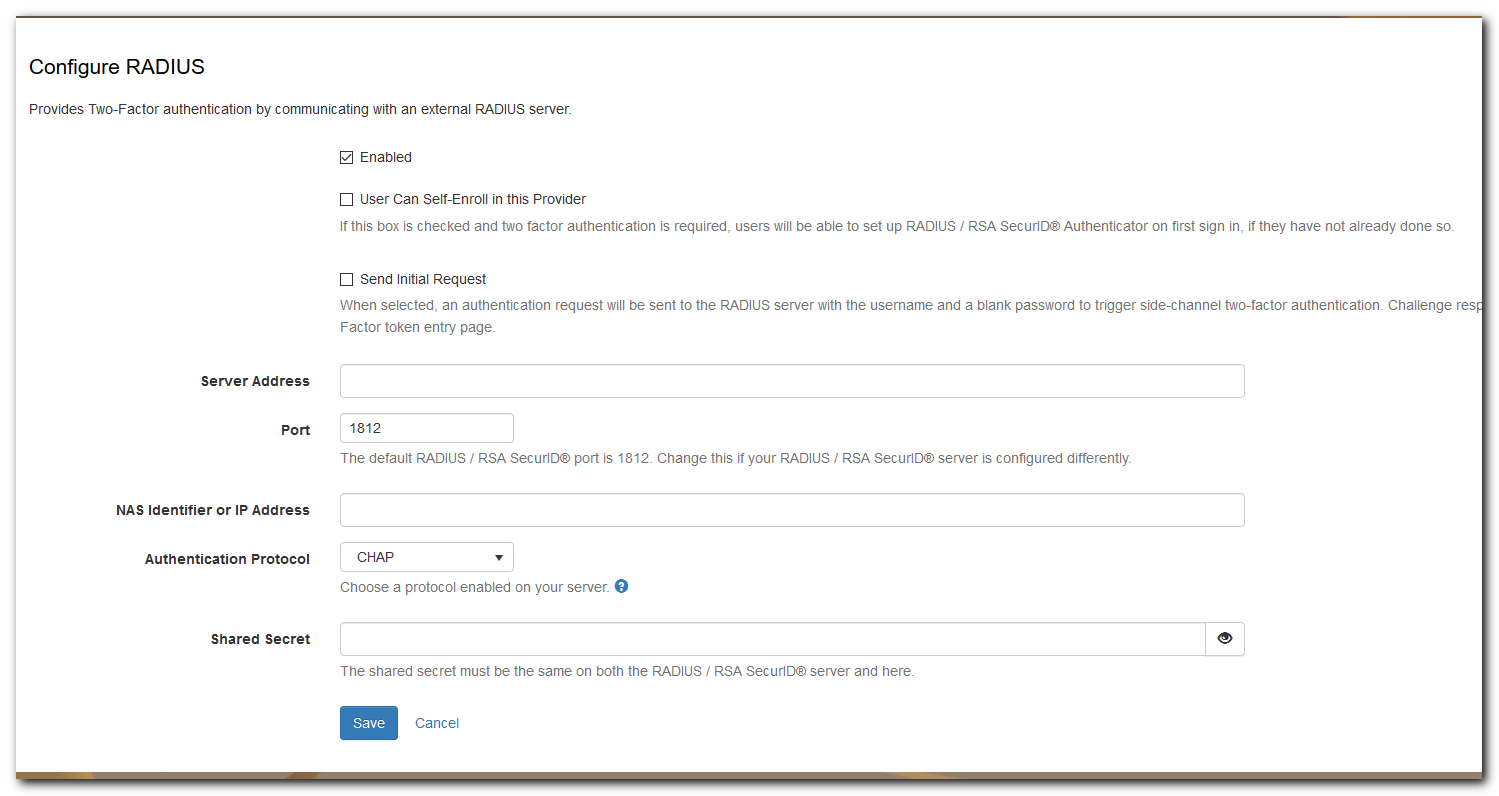
- Using the details required by RSA SecurID, fill in the fields:
- Set Enabled to True
- Set "User Can Self-Enroll in this Provider"
- Server Address
- Server Port
- Select an Authentication Protocol - enabled for RSA SecurID
- See: available protocols
- Shared Secret
- Click Save.
Attach and Enroll Users
Additional Users can be attached to this policy by either:
- Setting a Role policy: from Policies -> Set the Role Policy or Edit -> Set Policy
- Setting a User's policy: From Manage Users -> Click User name -> Edit -> Change policy
-
Setting it as the Users' default Policy: From Policies -> Edit -> Global Settings -> Set the Default Policy
Disabled: Users attached to the policy will show as disabled, until they are enabled or enrolled or self-enrolled.
Enabling 2FA for a User
Two-Factor Authentication can also be enabled individually for all users you would like to authenticate against a RADIUS server:
- Go to Users and Roles > Manage Users and click the name of the user you want to enable RADIUS for.
- Scroll down to Policy Information and look for RADIUS in the Two Factor Authentication list. Click the [Configure] link in that row.
- Click the Enable button on that screen. The user will now be prompted for a password for the RADIUS server each time they log in.
- If RADIUS needs to be disabled for a user, you can go back to the previous screen and a Disable button will be present instead of the Enable button.
User Configuration and Self-Enrollment
The prompt is the same: for user configuration setup, and subsequently, for each time they use 2FA:
-
"Please enter the one-time password or secret code."
Configuration error:
-
"RADIUS configuration failed. Please try again"
Token entry error:
-
"Invalid two-factor token. Please try again"
Using RADIUS via Duo
The support documentation on Duo's website has instructions for setting up the Duo proxy service as a RADIUS server or client.
Setup Requirement: The only requirement for using this setup with Password Server is that PAP must be selected as the authentication protocol in the policy configuration.
When a user logs in, they must type in both their password and Duo token as described in Duo's documentation here. If you are using the Duo-only client, this is unnecessary; users just need to type in their Duo token to authenticate.