Microsoft Entra ID (formerly Azure AD)
Website Documentation for your KeePass client and Pleasant Password Server
Password Server provides integration directly with Microsoft Entra Directory Services (formerly Azure AD). Authenticated Users of Office 365 or Microsoft Entra ID, are authorized through this Trusted Identity Provider to access Pleasant Password Server.
- The Microsoft Entra ID integration requires users to be setup or imported:
- local users setup in Password Server, or
- directory users imported from AD/LDAP, or
- directory users in Microsoft Entra Domain services, with 'lift and shift' from AD/LDAP domain controllers
- Currently pure Microsoft Entra queries are not yet supported.
Since Microsoft Entra provides a proprietary password reset, the Pleasant Password Server Reset Server module is not needed. Please inquire if you wish to use an alternative to the Microsoft Entra reset method.
*Authenticated access* - publish internal applications externally, ensuring that only authenticated connections hit your network ("pre-authentication" setting option)
Have Questions? Contact Us!
Related:
Article Applies to:
- Versions 7.9.9+, Enterprise or higher
Why use Microsoft Entra ID (formerly Azure AD)?
Microsoft Entra Domain Services:
- Now provides managed domain services that are fully compatible with Windows Server Active Directory, such as: LDAP, Kerberos/NTLM authentication, group policy, domain join, etc.
- Works seamlessly regardless of whether your Microsoft Entra tenant is synced with your on-premises Active Directory or is cloud-only.
- Enables you to consume these domain services, without the need for you to deploy, manage and patch domain controllers in the cloud.
- Integrates with your existing Microsoft Entra tenant, thus making it possible for users to login using their corporate credentials.
- Additionally, you can use existing groups and user accounts to secure access to resources, thus ensuring a smoother ‘lift-and-shift’ of on-premises resources to Azure Infrastructure Services.
Prerequisites
- Requires Contributor privileges in the Azure subscription
- An Microsoft Entra ID tenant with:
- An active subscription
- Global Administrator privileges
- Configured for self-service password reset:
Setup Overview
- Step 1 - Configure Microsoft Entra Domain Services
- Step 2 - Configure LDAPS for Microsoft Entra DS
- Step 3 - Configure Password Server
Step 1 - Configure Microsoft Entra Domain Services
Configure Microsoft Entra Domain Services for your Microsoft Entra tenant
1. Sign in to the Azure Portal

2. Create an Instance
To launch the Enable Microsoft Entra Domain Services wizard, complete the following steps:
- In the upper left-hand corner of the Azure portal, select + Create a resource.
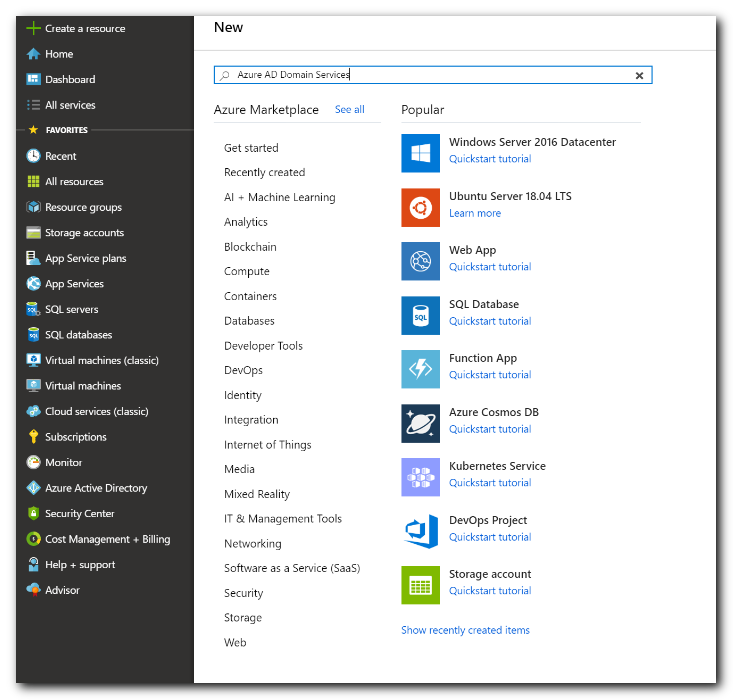
- Enter Domain Services into the search bar, then choose Microsoft Entra Domain Services from the search suggestions.
- On the Microsoft Entra Domain Services page, select Create.
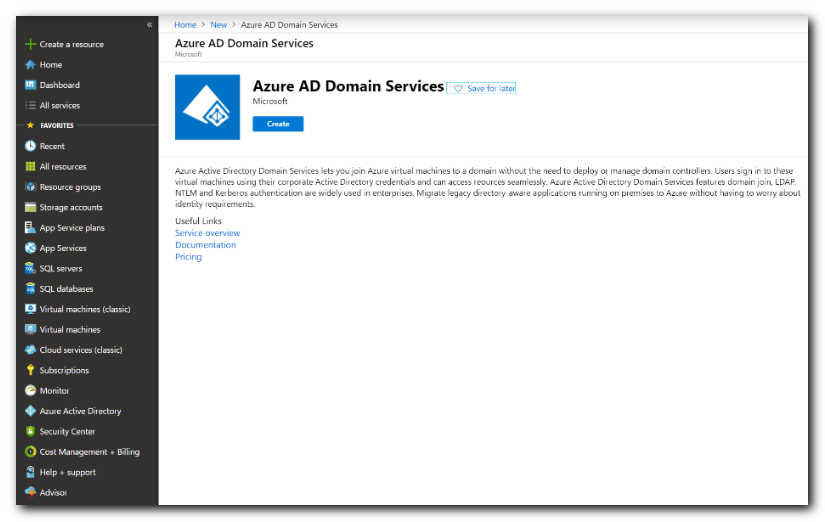
- The Enable Microsoft Entra Domain Services wizard is launched.
- The DNS domain name you select DOES NOT need to be the same as the Microsoft Entra domain
- Microsoft Entra DS limits the domain prefix to 15 characters
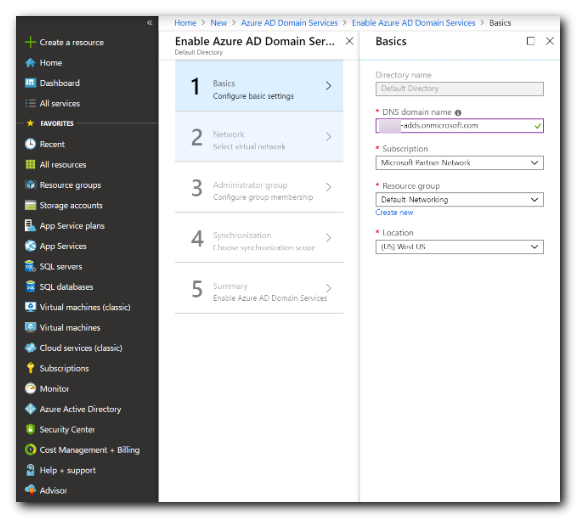
- Select the Azure Subscription in which you would like to create the managed domain.
- Select the Resource group to which the managed domain should belong.
- Choose to Create new or select an existing resource group.
- Choose/Create the virtual network.
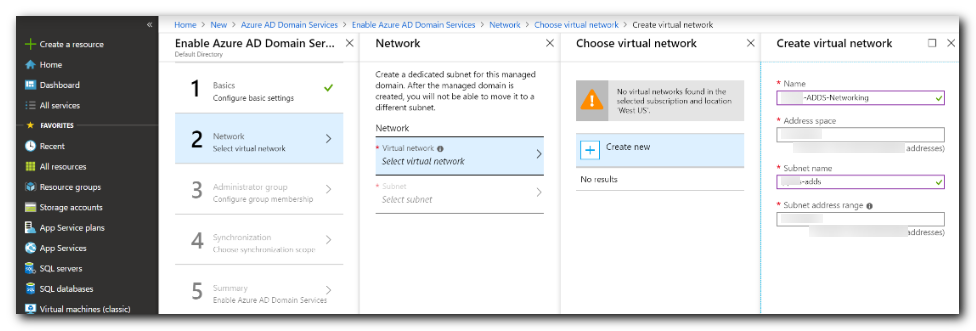
- If you're creating a new virtual network:
- Click ok, then the wizard will fill in the Virtual network and subnet fields.
- Click ok again.
- Next we will configure the Administrator Group.
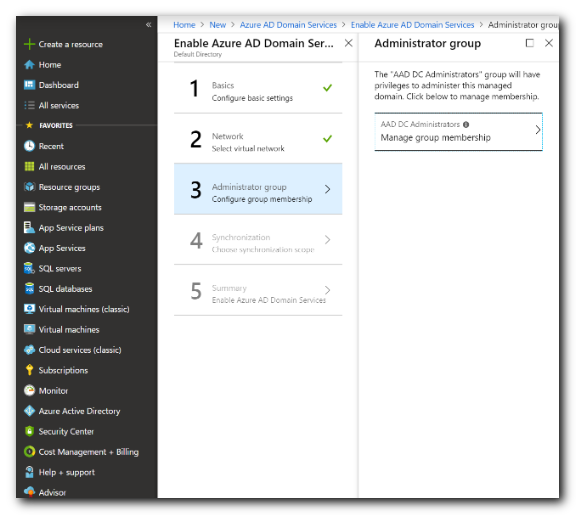
- Click Manage Group membership
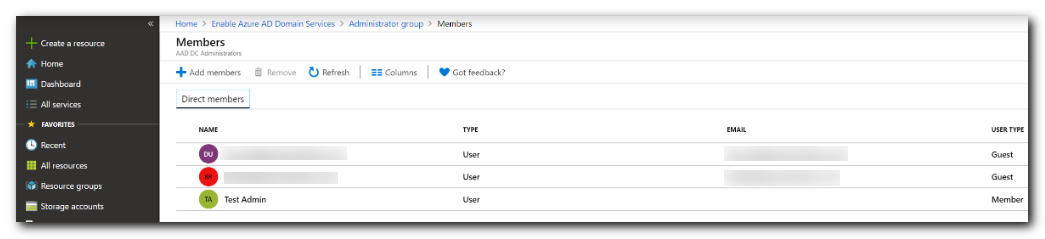
- Click Manage Group membership
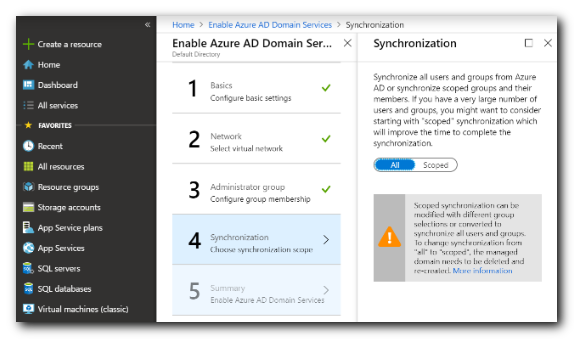
- Next you'll choose whether you want "all" or "scoped" synchronization.
- If the Microsoft Entra ID contain many users, or all users do not need to be accessible to Password Server, the select Scoped for Synchronization.
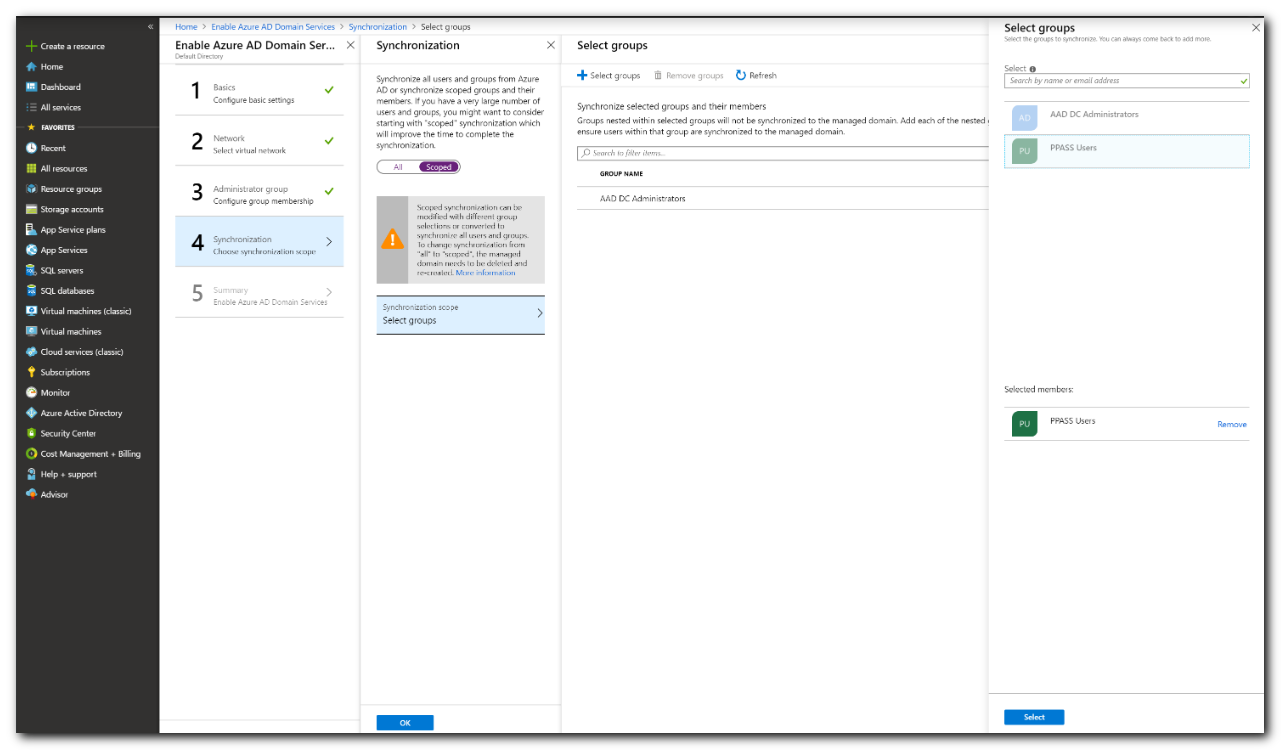
- If unsure, select Scoped as you cannot change from All to Scoped without deleting and re-creating the Microsoft Entra DS server.
- On the Summary page of the wizard, review the configuration settings for the managed domain.
- You can go back to any step of the wizard to make changes.
- If everything looks good hit "ok."
Deploy the managed domain
The process of provisioning your managed domain can take up to an hour. A notification is displayed in the portal that shows the progress of your Microsoft Entra DS deployment. Select the notification to see detailed progress for the deployment.
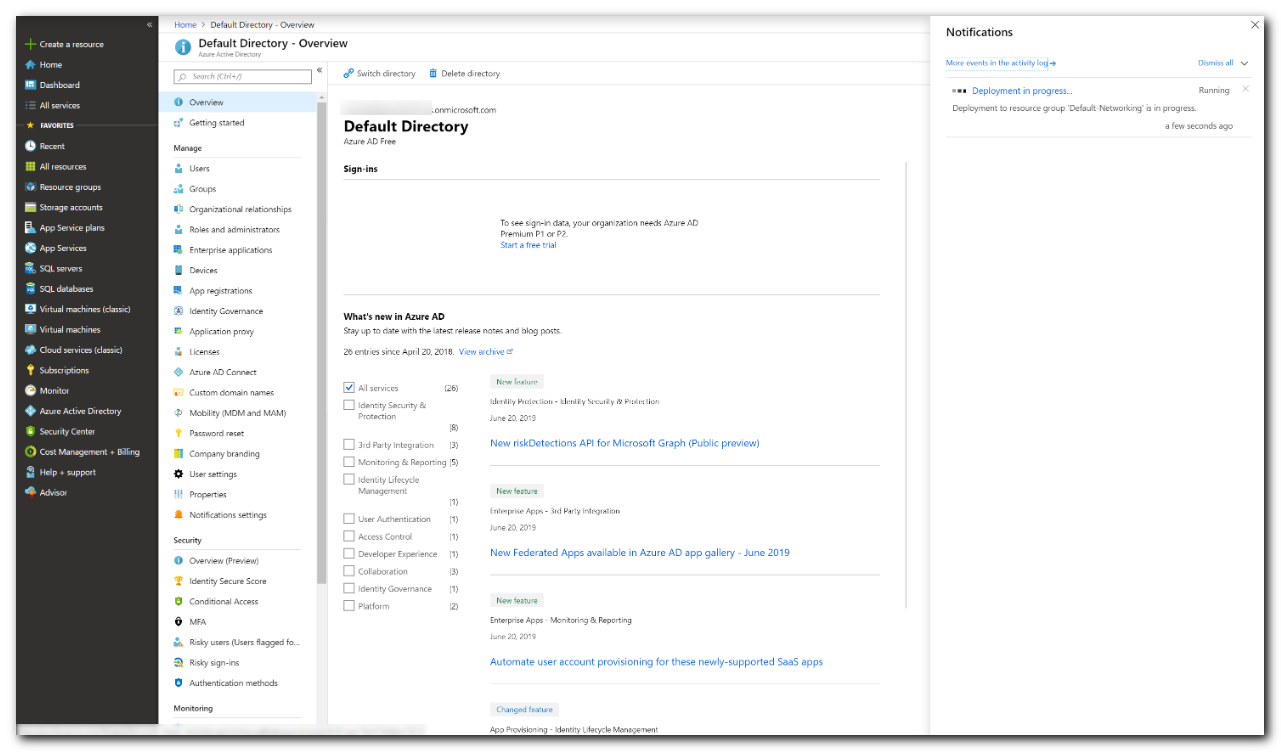
The page will load with updates on the deployment process, including the creation of new resources in your directory.
Select your resource group, such as myResourceGroup, then choose your Microsoft Entra DS instance from the list of Azure resources, such as contoso.com. The Overview tab shows that the managed domain is currently Deploying. You can't configure the managed domain until it's fully provisioned.
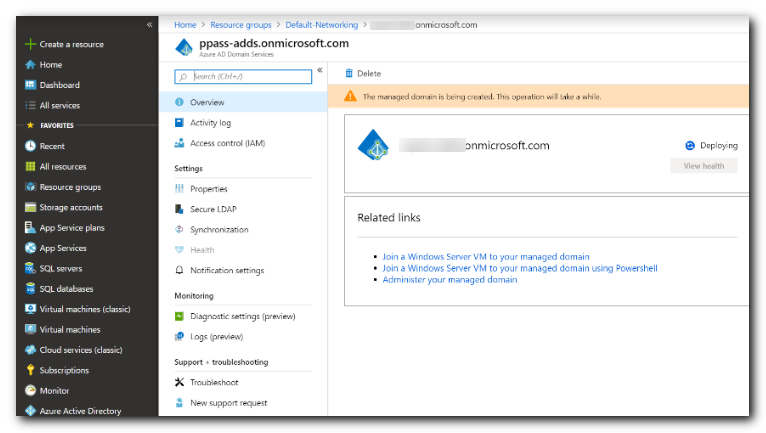
When the managed domain is fully provisioned, the Overview tab shows the domain status as Running.
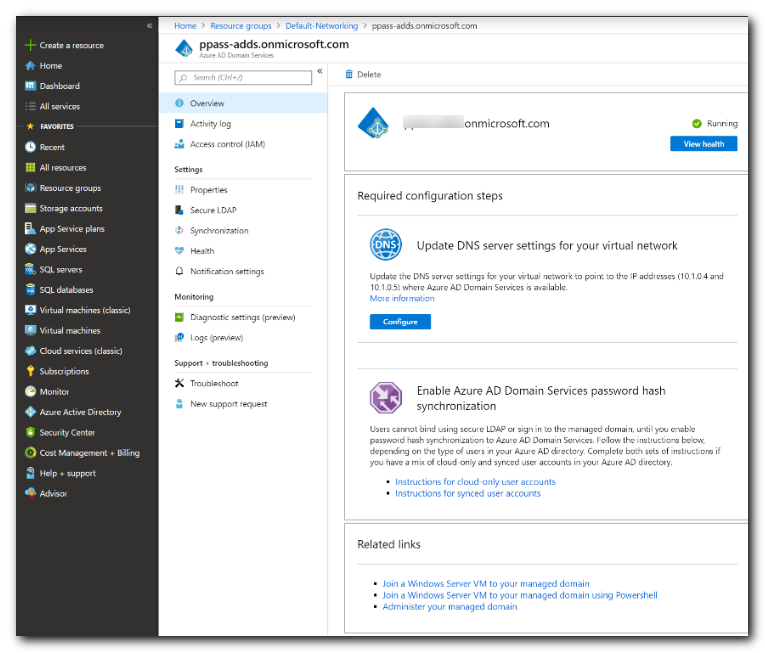
The managed domain is associated with your Microsoft Entra tenant. During the provisioning process, Microsoft Entra DS creates two Enterprise Applications named Domain Controller Services and AzureActiveDirectoryDomainControllerServices in the Microsoft Entra tenant. These Enterprise Applications are needed to service your managed domain. Don't delete these applications.
Step 2 - Configure LDAPS for Microsoft Entra DS
Create a valid self-signed certificate with the following steps:
- Note: Since you do not own the onmicrosoft.com domain, you will be unable to purchase a certificate for this domain.
- Setting up a Self-Signed Certificate
- This certificate will need to be installed on the machine hosting password server
- The DNS name of the certificate should match the DNS name of the Microsoft Entra DS server
- The DNS name of the certificate must match the DNS name that the LDAPS external IP address is bound to
- Modifying the HOSTS file of the machine that Password Server is hosted on is sufficient for DNS redirect
Enable secure LDAP for Microsoft Entra ID DS
Once the digital certificate is created and exported (including the private key), and the client computer is set to trust the connection...
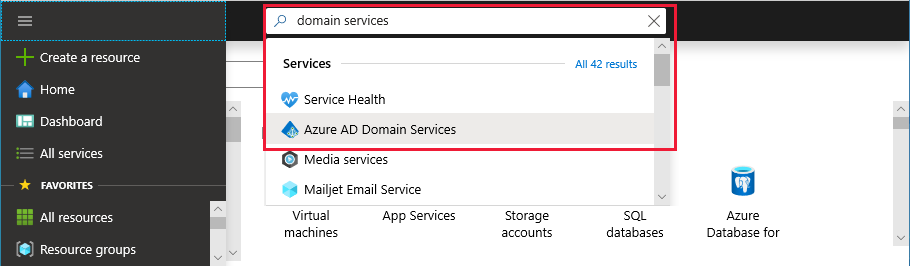
Now enable secure LDAP on your Microsoft Entra ID DS managed domain, by performing the following configuration steps:
- In the Azure portal, enter domain services in the Search resources box. Select Microsoft Entra Domain Services from the search result.
-
Choose your managed domain, such as contoso.com.
-
On the left-hand side of the Microsoft Entra DS window, choose Secure LDAP.
-
By default, secure LDAP access to your managed domain is disabled. Toggle Secure LDAP to Enable.
-
Secure LDAP access to your managed domain over the internet is disabled by default.
- Note: When you enable public secure LDAP access, your domain is susceptible to password brute force attacks over the internet. In the next step, a network security group is configured to lock down access to only the required source IP address ranges.
-
Toggle Allow secure LDAP access over the internet to Enable.
-
Select the folder icon next to .PFX file with secure LDAP certificate. Browse to the path of the .PFX file, then select the certificate created in a previous step that includes the private key.
As noted in the previous section on certificate requirements, you can't use a certificate from a public CA with the default .onmicrosoft.com domain. Microsoft owns the .onmicrosoft.com domain, so a public CA won't issue a certificate. Make sure your certificate is in the appropriate format. If it's not, the Azure platform generates certificate validation errors when you enable secure LDAP.
-
Enter the Password to decrypt .PFX file set in a previous step when the certificate was exported to a .PFX file.
-
Select Save to enable secure LDAP.
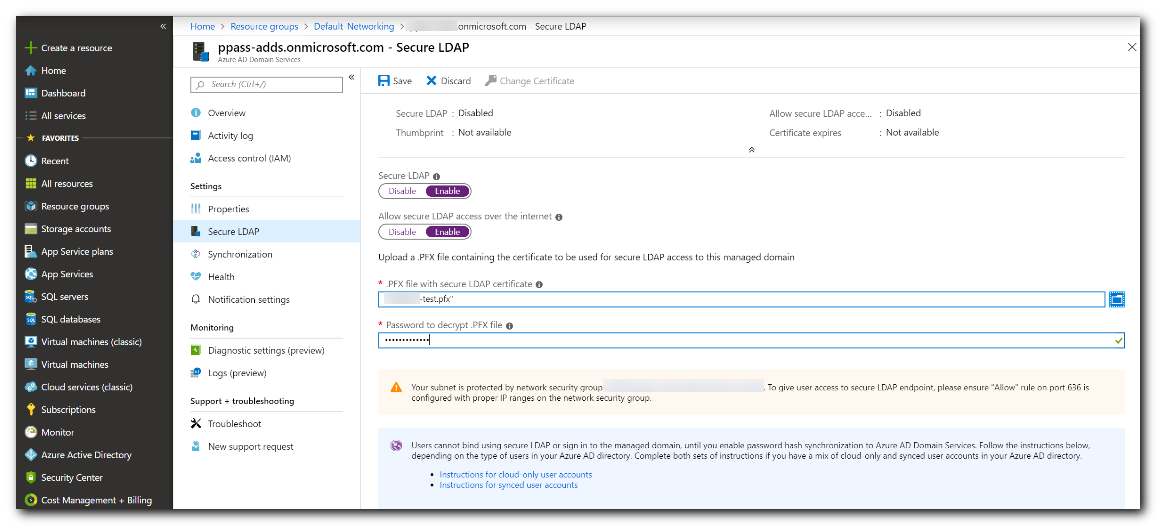
A notification is displayed that secure LDAP is being configured for the managed domain. You can't modify other settings for the managed domain until this operation is complete.
It takes a few minutes to enable secure LDAP for your managed domain. If the secure LDAP certificate you provide doesn't match the required criteria, the action to enable secure LDAP for the managed domain fails. Some common reasons for failure are if the domain name is incorrect, or the certificate expires soon or has already expired. You can re-create the certificate with valid parameters, then enable secure LDAP using this updated certificate.
Lock down secure LDAP access over the internet
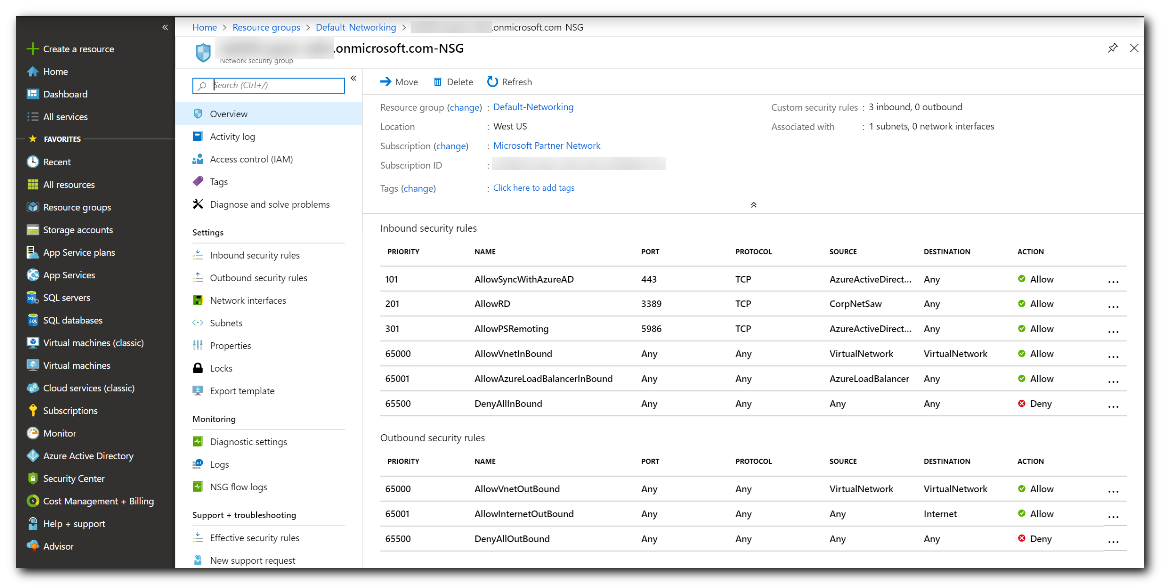
When you enable secure LDAP access over the internet to your Microsoft Entra DS managed domain, it creates a security threat. The managed domain is reachable from the internet on TCP port 636. It's recommended to restrict access to the managed domain to specific known IP addresses for your environment. An Azure network security group rule can be used to limit access to secure LDAP.
Let's create a rule to allow inbound secure LDAP access over TCP port 636 from a specified set of IP addresses. A default DenyAll rule with a lower priority applies to all other inbound traffic from the internet, so only the specified addresses can reach your Microsoft Entra DS managed domain using secure LDAP.
-
In the Azure portal, select Resource groups on the left-hand side navigation.
-
Choose you resource group, such as myResourceGroup, then select your network security group, such as aaads-nsg.
-
The list of existing inbound and outbound security rules are displayed. On the left-hand side of the network security group windows, choose Security > Inbound security rules.
-
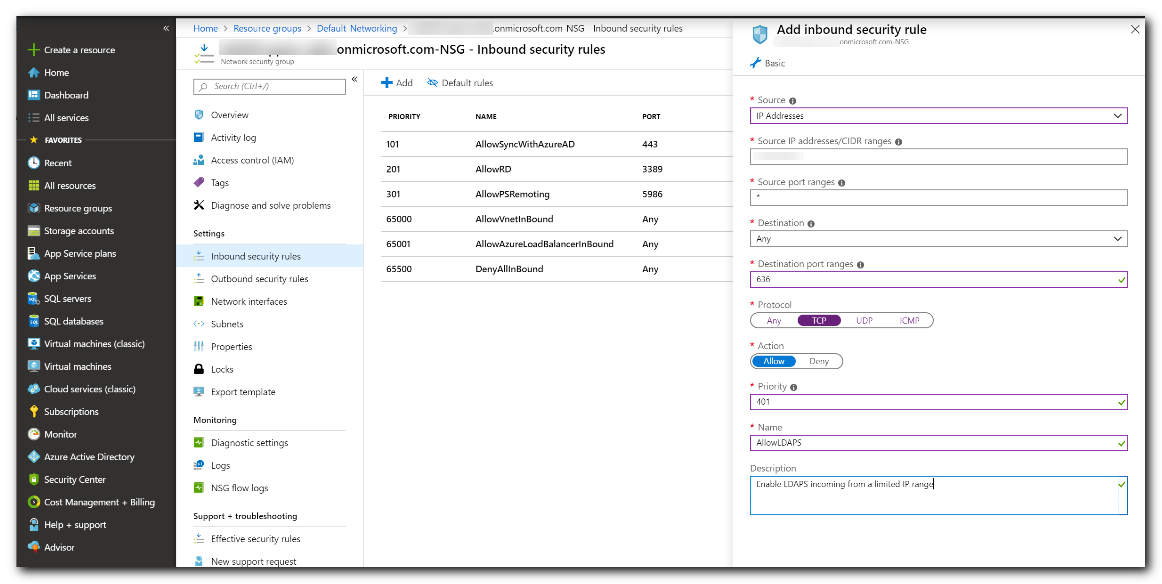
Select Add, then create a rule to allow TCP port 636. For improved security, choose the source as IP Addresses and then specify your own valid IP address or range for your organization.
- When ready, select Add to save and apply the rule.
Step 3 - Configure Password Server
Configuring Password Server
- Authentication Type will be Microsoft Negotiate
- Host will be the DNS name you have bound to the Secure LDAP external IP address
- Note The DNS name must be the same one the LDAPS certificate was issued for, and the certificate must be trusted
- Port will be 636 and Use SSL must be enabled
- Provide a username and password for a user in the domain
- Leave Allow Password Changes unchecked
- Recommended Set the User Relative DN and Group Relative DN (advanced settings) to:
- OU=AADDC Users
Microsoft Entra Connect
- Not covered here, but this optional module allows an on-premises AD DS server to sync (two-way) with an Microsoft Entra tenant
- When combined with Microsoft Entra DS this would allow for users that exist in the on-premises server to bind to the Azure LDAPS server
- If you have an on-premises server it may be better to sync Password Server directly to that
References:
- Configure Microsoft Entra Domain Services
- Configure LDAPS for Microsoft Entra DS
- How synchronization works
