Access Levels
Discover how Pleasant Password Server will enhance KeePass for business
Access Levels are customizable.
You can define the levels of access you want to shape how your Users and Roles can interact with Folders and Entries. This allows the access to be specified once, and then to be reused as you assign access for your teams and individuals. Access Levels are assigned as a complete set to the user or role.
- Access Levels combines a set of allowed Actions and Grants
- an Action allows the user to perform the action
- a Grant allows the user to give the action to other users
Access is Inherited
The access on a folder gets inherited to contents below, including the folders and entries. However, this inherited access can be blocked on a folder/entry, and then the folder/entry and any items included under it will not inherit the blocked access.
For example:
- "Full" access on a folder means "Full" access to all of the contents underneath the folder, including Entries, Subfolders, sub-Subfolders, etc. (unless that inheritance is explicitly Blocked).
Have Questions? Contact Us!
Assigning Access Levels
Access levels are assigned on a Folder or Entry to a user or role to become effective.
Modifying Access Levels
Access Levels can be viewed or modified from the Web Admin client here:
-
Navigation menu -> Access Levels
Community editions do not allow the default Access Levels to be modified.
Default Access Levels
Enterprise Edition or higher:
- Full
- Full + Grant
- Full + Grant + Block
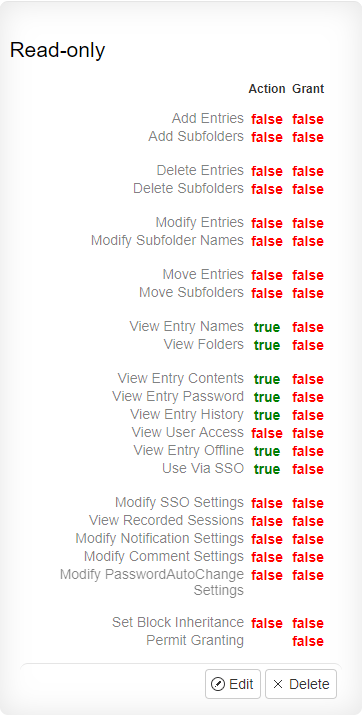
- Read-Only
- ... plus ability to create more...
These editions allow the ability to flexibly create or modify Access Levels (via the "Access Levels" tab).
Community Edition:
- Full
- Full + Grant
- Full + Grant + Block
Included in all editions
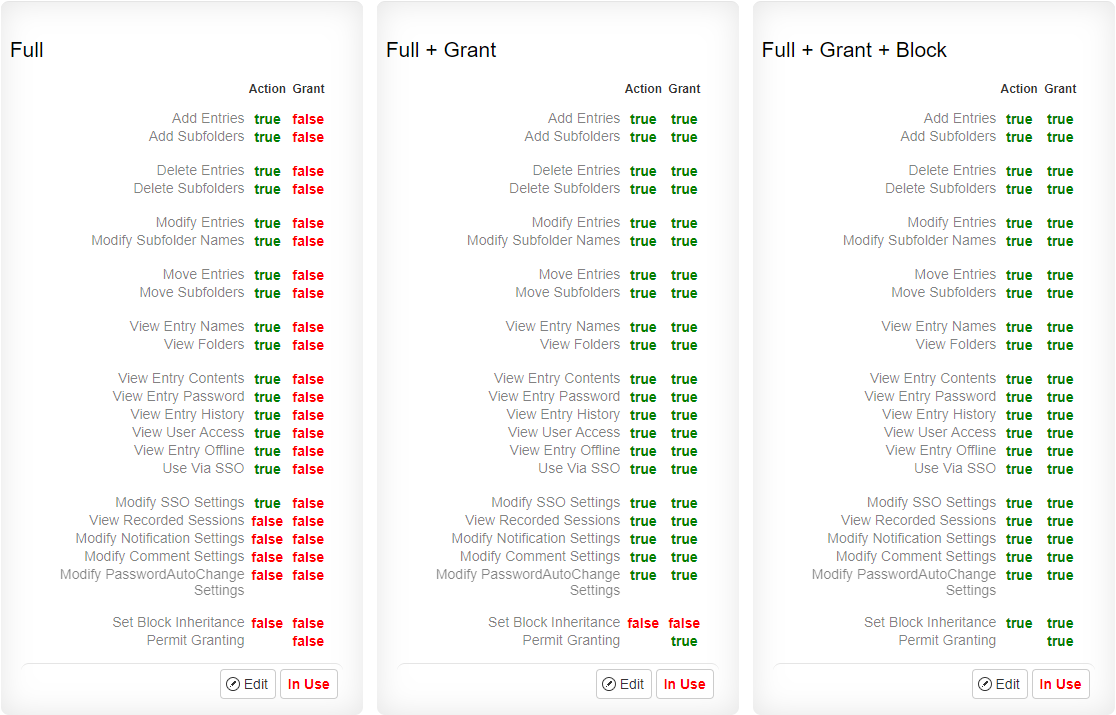
Included in Enterprise edition or higher
Block Inherited Access
Be sure to double-check User Access settings prior to setting Block Inheritance.
Typically, the following Access types are inherited:
-
Modify Entries, Modify Proxy Settings, View Entry Contents, View Entry Password, View Entry History, Use Via SSO, Set Block Inheritance
If you decide to block inheritance on an entry or folder without directly re-adding these access types, you will then lose the ability to perform these actions.
Explanation: The listed access types apply to the entry or folder they are set on.
Restore Inherited Access
By default admins can restore inheritance if they have the following permissions on the object (default setting):
- Set Block Inheritance: Action = True, and Grant = True
-
Set Permit Granting: Grant = True
Steps - to create a "Restore Inheritance" access level:
- In the web client navigate to: Access Levels tab.
- Click Add New Access Level to create a custom access level
- Add the permissions (mentioned above)
- Set Block Inheritance: Action = True, and Grant = True
-
Set Permit Granting: Grant = True
Only provide this Access to a trusted user/role, e.g. to admin.
It is also possible to make this access only available upon request, using the Request-Approve workflow.
List of Access Actions
| Action | Notes |
| Add Entries | |
| Add Subfolders | |
| Permanently Delete Entries | Applied on folders only (no effect if directly applied on an entry). |
| Permanently Delete Subfolders | |
| Archive Entries | |
| Archive Subfolders | |
| Modify Entries | Allows: modifying all fields (web client only: modifying password also requires View Entry Password), adding and removing attachments. |
| Modify Subfolder Names1 | |
| Move Entries | Applies to folders only (no effect if directly applied to entry). Must be enabled on source and destination. |
| Move Subfolders | Must be enabled on source and destination. |
| View Entries | Required to make an entry visible at all (Web client only: visibility outside of search also requires View Folders on the containing folder). |
| View Folders | This allows a user to know that a folder exists and see its names. |
| Request Access | |
| View Entry Contents |
Everything except the password and title. Web client only: users without View Entry Password must also lack Modify Entries (or receive an error). |
| View Entry Password | Web client only: required to allow editing a password. |
| View Entry History | |
| View User Access (v7.5.3+) | Controls User Access window visibility for users without Grant access on the target entry/folder (those with Grant access can always see the User Access window). |
| View Entry Offline (v7+) | Controls visibility in the KeePass Client's Offline Mode. |
|
Use Via SSO Proxy (v7.3.1+) / |
Displays SSO Server tab, allows usage of SSO. |
| View TOTP Settings | |
| Modify TOTP Settings | |
| Modify SSO Settings (v7.3.1+) / Modify Proxy Settings (v7.2.6-) | Proxy/SSO settings are inherited just like access. |
| View Recorded Sessions | Allows viewing of Recorded SSO Sessions for permitted entries |
| Modify Notification Settings (v7+) | Allows attaching/detaching existing Notification Triggers. Attached triggers are inherited just like access. |
| Modify Comment Settings (v7+) | Allows attaching/detaching existing Comment Triggers. Attached triggers are inherited just like access. |
| Modify PasswordAutoChange Settings (v7.0.16+) | Allows creating, editing, and choosing among Credential Hosts. Credential Hosts are inherited like access, with one difference: they can be deleted at any level in the inheritance tree. |
| Set Block Inheritance | Block or Unblock Inheritance |
| Permit Granting | Grant only. Changes all other G access rows so they permit themselves and the corresponding A's to be assigned (rather than only the latter). This allows a user to Grant access levels which have Grant access rows. |
1 - The ability to rename the Root folder is controlled by the Global Settings role permission:
- Users and Roles -> Manage Roles -> Actions dropdown -> Set Permissions
Move Actions
Move Entries and Move Subfolders behave slightly differently than other access types. In addition to the requirements listed above, the mover needs to have:
- Grant access for both source and destination for each action and for any users and roles that will be gaining access.
